Trust negotiation is a dynamic process where two entities establish trust in each other by exchanging and evaluating digital credentials. This process helps to facilitate secure interactions in the online world without the need for prior relationships. As online interactions continue to expand, trust negotiation plays a critical role in ensuring secure and trustworthy exchanges. Trust negotiation helps protect user privacy, prevent fraud, and build confidence in digital services. The trust negotiation process can be broken down into three phases: Initiation, Credential Exchange, and Trust Establishment. The initiation phase sets the groundwork for the trust negotiation process. It involves two primary steps: Before any credentials or trust requirements are exchanged, a secure communication channel must be established between the two parties. This ensures that the negotiation process is not vulnerable to eavesdropping or tampering. In this step, both parties introduce themselves and provide basic information about their identities. This may involve exchanging digital certificates that include public keys and other identifying information. Once the parties are identified, they can proceed to the next phase. During the credential exchange phase, parties present and evaluate each other's credentials. This phase consists of two steps: Each party presents its digital credentials to the other. These credentials can include anything from digital certificates to attestations from third parties, such as government agencies or certification authorities. The credentials serve as proof of the party's trustworthiness and can also contain information about the party's capabilities and privileges. Upon receiving the credentials, each party must evaluate their authenticity and relevance. This involves checking the credentials' signatures, ensuring they are issued by trusted entities, and determining whether they meet the trust requirements set by both parties. If the credentials pass the evaluation, the process moves to the next phase. The trust establishment phase is the final step in the trust negotiation process. It consists of two steps: Both parties assess the overall trust level based on the exchanged credentials and trust requirements. This evaluation can involve weighing the importance of different credentials and considering any additional factors that might influence trust. Once the trust level evaluation is complete, the parties must decide whether to proceed with the interaction or terminate the negotiation. If both parties are satisfied with the trust level, they can reach an agreement and begin their collaboration. However, if the trust level is insufficient, or if any of the trust requirements are not met, the negotiation process may end in termination. Credential disclosure is a fundamental aspect of credential-based trust negotiation. It involves presenting digital proofs or assertions to demonstrate identity, qualifications, or permissions, which are then evaluated by the receiving party. Verification is a crucial step in credential-based trust negotiation. It involves the receiving party authenticating and validating the disclosed credentials to ensure their legitimacy and relevance to the trust negotiation. Reputation systems play a significant role in reputation-based trust negotiation. They collect and analyze user feedback and behavior data to generate trust scores, which help parties evaluate the trustworthiness of potential partners. Trust scores and feedback provide quantitative and qualitative insights into an entity's trustworthiness. These metrics enable parties to make informed decisions during reputation-based trust negotiations. Hybrid trust negotiation models combine elements of credential and reputation-based systems to provide a more comprehensive and flexible approach to establishing trust. These models enable parties to leverage the strengths of both approaches, enhancing overall trust negotiation effectiveness. Adaptive trust negotiation is an advanced form of hybrid trust negotiation that adjusts the negotiation process based on contextual factors. This approach increases efficiency and effectiveness by dynamically adapting to the needs and preferences of the parties involved. Trust-X is a bilateral trust negotiation protocol that enables secure and privacy-preserving credential exchange between parties. The protocol uses a rule-based approach to negotiate trust iteratively, providing a flexible and scalable solution for trust establishment. Trust-Serv is a service-oriented bilateral trust negotiation protocol that simplifies trust management in service-based environments. It uses a modular design and supports various credential types, allowing for seamless integration with different service architectures. PeerTrust is a distributed trust negotiation protocol designed for peer-to-peer (P2P) environments. It utilizes a decentralized approach to trust management, leveraging local trust relationships and global reputation data to enable efficient trust establishment. TrustGuard is a distributed trust negotiation protocol that focuses on providing security and privacy in ad-hoc and mobile networks. The protocol uses a combination of local trust information and cryptographic techniques to protect sensitive data during trust negotiation. TrustBuilder is a privacy-preserving trust negotiation protocol that enables the secure and anonymous exchange of credentials. It employs cryptographic techniques such as zero-knowledge proofs to protect sensitive information during the negotiation process. PGP-based trust negotiation employs the Pretty Good Privacy (PGP) protocol to facilitate trust establishment. It leverages PGP's web of trust model and its cryptographic techniques to ensure secure and privacy-preserving communication between negotiating parties. One challenge in trust negotiation is establishing trust when parties have no prior relationships. Solutions include using credential-based models to prove qualifications or relying on reputation systems to evaluate an entity's trustworthiness based on past interactions and feedback. Privacy-enhanced trust negotiation focuses on protecting sensitive information during trust negotiation. Techniques such as zero-knowledge proofs, secure multi-party computation, and anonymization help maintain privacy while allowing parties to establish trust. Selective disclosure of credentials enables parties to control the information they share during trust negotiation. By revealing only the necessary credentials, parties can balance trust establishment with privacy concerns, minimizing potential data exposure. Time-sensitive trust negotiation addresses the need for quick trust establishment in dynamic environments. By prioritizing certain credentials or using reputation data for fast decision-making, parties can expedite the trust negotiation process and adapt to changing conditions. Continuous trust evaluation monitors and updates trust levels throughout an ongoing relationship. This approach ensures that trust remains relevant and accurate, accounting for changes in behavior or circumstances that may impact a party's trustworthiness. Trust negotiation plays a critical role in e-commerce and online marketplaces by ensuring secure transactions and protecting user privacy. By establishing trust between buyers and sellers, trust negotiation promotes confidence in the platform and helps prevent fraud. In collaborative platforms and online communities, trust negotiation facilitates secure information sharing and collaboration. It enables users to confidently engage with others, knowing their data is protected and shared only with trustworthy parties. Trust negotiation is essential in IoT and smart device ecosystems to ensure secure communication and data exchange. By establishing trust between devices and users, trust negotiation helps maintain privacy and security in an increasingly connected world. In blockchain and decentralized systems, trust negotiation enables secure and privacy-preserving interactions among participants. By establishing trust between parties, trust negotiation supports the secure exchange of assets and information in these distributed environments. Trust negotiation is essential for secure online interactions and helps build confidence in digital services. Various models, such as credential-based, reputation-based, and hybrid models, enable parties to establish trust in different contexts. Various trust negotiation protocols have been developed, addressing bilateral, distributed, and privacy-preserving needs. In the digital era, trust negotiation has become increasingly important as online interactions continue to grow. From e-commerce and online communities to IoT and blockchain systems, trust negotiation is essential for maintaining security, privacy, and confidence in a wide range of applications. As technology continues to advance, it is vital to invest in further research and development in trust negotiation. By exploring new models, protocols, and techniques, we can continue to enhance trust establishment, ensuring secure and reliable interactions in an increasingly interconnected world.What Is a Trust Negotiation?
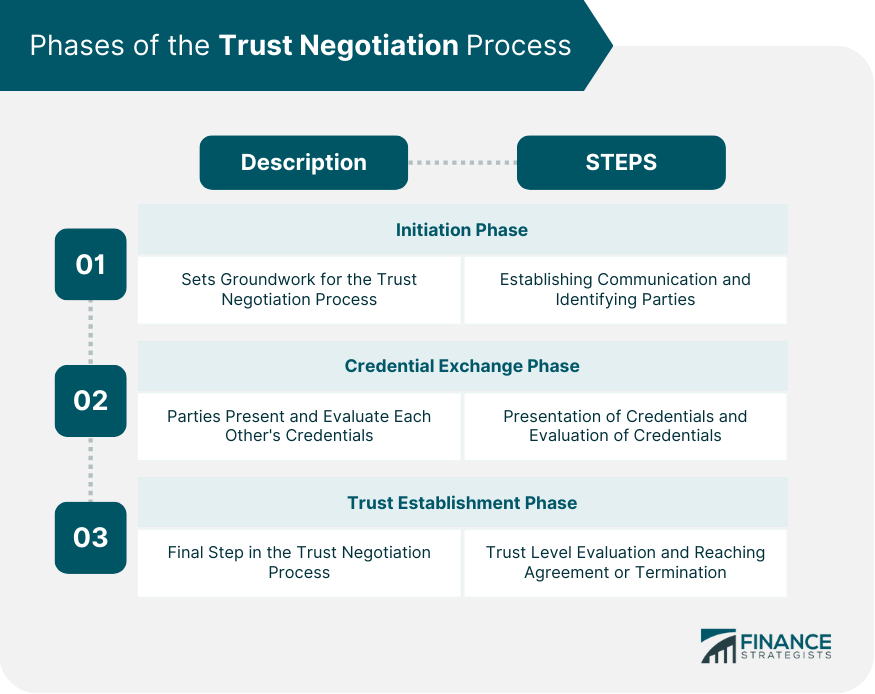
Phases of the Trust Negotiation Process
Initiation Phase
Establishing Communication
Identifying Parties
Credential Exchange Phase
Presentation of Credentials
Evaluation of Credentials
Trust Establishment Phase
Trust Level Evaluation
Reaching Agreement or Termination
Trust Negotiation Models
Credential-Based Trust Negotiation
Credential Disclosure
Credential Verification
Reputation-Based Trust Negotiation
Reputation Systems
Trust Scores and Feedback
Hybrid Trust Negotiation Models
Combining Credential and Reputation-Based Systems
Adaptive Trust Negotiation

Trust Negotiation Protocols
Bilateral Trust Negotiation Protocols
Trust-X
Trust-Serv
Distributed Trust Negotiation Protocols
PeerTrust
TrustGuard
Privacy-Preserving Trust Negotiation Protocols
TrustBuilder
PGP-Based Trust Negotiation
Challenges and Solutions in Trust Negotiations
Establishing Trust in the Absence of Prior Relationships
Balancing Trust and Privacy Concerns
Privacy-Enhanced Trust Negotiation
Selective Disclosure of Credentials
Handling Trust Negotiations in Dynamic and Open Environments
Time-Sensitive Trust Negotiation
Continuous Trust Evaluation
Trust Negotiation Applications
E-Commerce and Online Marketplaces
Collaborative Platforms and Online Communities
Internet of Things (IoT) and Smart Devices
Blockchain and Decentralized Systems
Final Thoughts
Trust Negotiation FAQs
Trust negotiation is a dynamic process where two entities establish trust by exchanging and evaluating digital credentials. It plays a crucial role in ensuring secure and trustworthy exchanges in online interactions, helping protect user privacy, prevent fraud, and build confidence in digital services.
Credential-based trust negotiation involves the exchange and verification of digital credentials to prove identity, qualifications, or permissions. Reputation-based trust negotiation, on the other hand, relies on reputation systems that collect and analyze user feedback and behavior data to generate trust scores, which help parties evaluate the trustworthiness of potential partners.
Some common trust negotiation protocols include Trust-X and Trust-Serv for bilateral trust negotiation, PeerTrust and TrustGuard for distributed trust negotiation, and TrustBuilder and PGP-based trust negotiation for privacy-preserving trust negotiation.
Trust negotiation ensures secure transactions and protects user privacy in e-commerce and online marketplaces by establishing trust between buyers and sellers. It promotes confidence in the platform, helps prevent fraud, and enables users to engage in transactions with trustworthy parties.
Future trends and research directions in trust negotiation include the use of AI and machine learning to automate and improve trust establishment, the development of cross-domain trust negotiation protocols, the exploration of trust negotiation in the era of quantum computing, and the consideration of ethical implications and human factors in trust negotiation processes.
True Tamplin is a published author, public speaker, CEO of UpDigital, and founder of Finance Strategists.
True is a Certified Educator in Personal Finance (CEPF®), author of The Handy Financial Ratios Guide, a member of the Society for Advancing Business Editing and Writing, contributes to his financial education site, Finance Strategists, and has spoken to various financial communities such as the CFA Institute, as well as university students like his Alma mater, Biola University, where he received a bachelor of science in business and data analytics.
To learn more about True, visit his personal website or view his author profiles on Amazon, Nasdaq and Forbes.