Double-spending in blockchain refers to a scenario where a user manages to spend the same digital token or cryptocurrency more than once. This is possible due to the fact that digital information can be reproduced relatively easily. Cryptocurrencies like Bitcoin were designed specifically to solve this problem and prevent double-spending, using a series of complex cryptographic algorithms and decentralized mechanisms. Within this context, double-spending can be understood as a potential flaw within a digital cash scheme, where a user fraudulently spends the same amount twice or more. This issue becomes particularly significant as the lack of a physical counterpart for digital tokens makes it hard to prevent one token being duplicated and used again. If left unresolved, double-spending can disrupt the integrity of the blockchain, lead to inflation by increasing the number of coins in circulation, and undermine trust in the cryptocurrency. When a transaction is conducted, it is added to a pool of unconfirmed transactions. Miners then select transactions from this pool to form a new block and add it to the blockchain. The double-spending issue arises when a user broadcasts two transactions into the network using the same coins. This user might send one transaction to a merchant, and another to themselves. Both transactions are unconfirmed at first and may be picked up by different miners. If the transaction to themselves gets confirmed first, the coins are returned to them, and the transaction to the merchant becomes invalid. Thus, the user manages to spend the same coins twice, hence 'double-spending'. In traditional monetary systems, double-spending is not an issue because physical currency cannot be easily duplicated. Moreover, banks and other financial institutions serve as intermediaries to verify transactions and ensure that the same money is not spent twice. However, these traditional systems come with their own problems. Intermediaries often charge fees for their services, and transactions can take time to process. Additionally, the need for intermediaries brings about issues of trust and centralization. The problem of double-spending becomes significant in the realm of digital currencies, due to the ease of duplicating digital information. In the absence of a physical entity that can be handed over from one person to another, ensuring that a digital token hasn't been spent twice becomes a challenge. This issue is amplified in decentralized digital currencies, such as Bitcoin. In these systems, there is no central authority to verify transactions and prevent double-spending. Instead, these tasks are performed by a decentralized network of peers. One of the main ways blockchain technology prevents double-spending is through the use of consensus algorithms. Consensus algorithms are a set of rules used to agree on the contents of a blockchain. Most notably, Bitcoin uses a consensus algorithm known as proof-of-work (PoW). In PoW, miners must solve a complex mathematical problem to add a new block to the blockchain. This requires significant computational resources, making it difficult for a single user to control the majority of the network's mining power, and thus preventing double-spending. Another mechanism used to prevent double-spending in blockchain is transaction verification. Before a transaction is added to the blockchain, it is verified by nodes in the network. They check the transaction against the blockchain to ensure that the coins being spent have not been spent before. If a double-spend is detected, nodes reject the fraudulent transaction. This verification process, combined with the transparency of the blockchain, makes it extremely difficult to double-spend in a blockchain system. In many blockchain systems, recipients can mitigate the risk of double-spending by waiting for a sufficient number of confirmations before considering a transaction complete. Each confirmation represents a new block added to the chain after the transaction, making it increasingly difficult to reverse. While waiting for more confirmations can increase security, it can also slow down transactions. As such, the optimal number of confirmations to wait for can depend on factors like the value of the transaction and the level of trust between the parties. In addition to the measures mentioned above, several network security measures also exist to prevent double-spending in blockchain. These include measures such as requiring nodes to solve a computational problem to join the network (Proof of Work), or having a selection of trusted nodes to validate transactions (Proof of Stake). Blockchain miners play a critical role in preventing double-spending. Miners are nodes in the blockchain network that validate new transactions and add them to the blockchain. They do this by solving complex computational problems, a process known as mining. By validating transactions and adding them to the blockchain, miners ensure that the same coins can't be spent twice. If a miner were to try to include a double-spend transaction in their block, other miners would reject the block, and the dishonest miner's effort would be wasted. A 51% attack refers to a potential attack on a blockchain network where a single entity or group gains control of more than half of the network's mining power. With the majority control, the entity could manipulate the blockchain ledger to their advantage and double-spend coins. The threat of a 51% attack emphasizes the importance of a decentralized network, where no single party has too much control. While theoretically possible, executing a 51% attack is extremely difficult in practice, due to the high cost and coordination required. In a Sybil attack, an attacker floods the network with nodes it controls, in an attempt to disrupt the network's functioning. If successful, the attacker could potentially double-spend by manipulating the transaction verification process. To prevent Sybil attacks, many blockchain networks require nodes to provide proof of work or proof of stake, which can be computationally or financially expensive for an attacker to replicate across many nodes. A Finney attack is a more sophisticated form of double-spending attack, named after Hal Finney, one of the early Bitcoin developers. In this attack, a miner mines a block including a transaction that pays them and does not broadcast this block. They then spend the same coins in a transaction to a merchant, who delivers goods upon seeing the transaction on the network. The attacker then broadcasts their previously mined block, invalidating the transaction to the merchant. Preventing Finney attacks requires merchants to wait for more confirmations before considering a transaction final. While not strictly a form of double-spending, counterfeiting risk is also a concern for blockchain networks. This involves an attacker creating fake coins that appear valid to the network. To prevent counterfeiting, all transactions in a blockchain network are thoroughly validated and cross-checked against the existing blockchain ledger. Double-spending in blockchain refers to a scenario where a user manages to spend the same digital token or cryptocurrency more than once. This issue arises due to the ability to easily duplicate digital information. Traditional monetary systems are not susceptible to double-spending because physical currency cannot be easily duplicated, and intermediaries, such as banks, verify and prevent duplicate spending. However, with digital currencies, ensuring that a digital token hasn't been spent twice becomes a challenge, especially in decentralized systems like Bitcoin. To address the double-spending problem, blockchain technology utilizes various prevention mechanisms. These include consensus algorithms like proof-of-work (PoW), transaction verification, waiting for sufficient confirmations, network security measures, and the role of miners. These mechanisms collectively work to ensure the integrity and security of transactions, making it extremely difficult to double-spend in a blockchain system.What Is Double-Spending in Blockchain?
How Does Double-Spending in Blockchain work
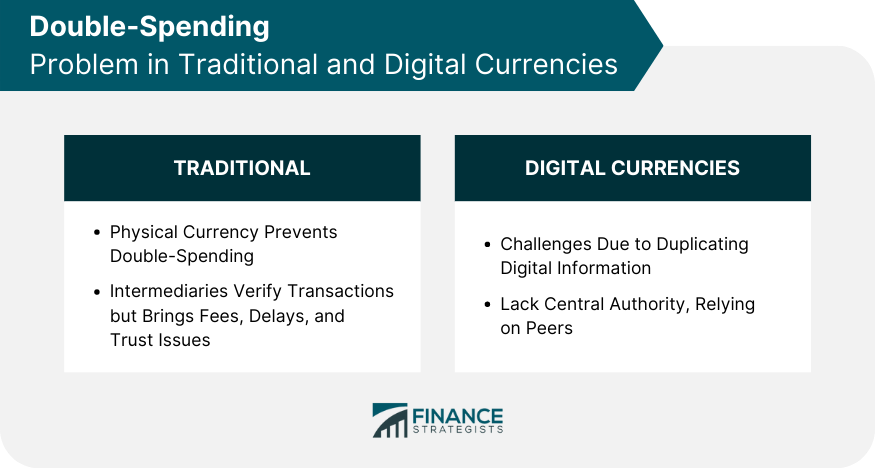
Double-Spending Problem
Traditional
Digital Currencies
Double-Spending Prevention Mechanisms
Consensus Algorithms in Blockchain
Transaction Verification
Waiting for Sufficient Confirmations
Network Security Measures
Role of Blockchain Miners

Double-Spending Risks and Attacks
51% Attack
Sybil Attack
Finney Attack
Counterfeiting Risk

Conclusion
Double-Spending in Blockchain FAQs
Double-spending in blockchain refers to a scenario where a user spends the same digital token or cryptocurrency more than once. This can be a significant issue for digital currencies as digital information can be easily duplicated.
Double-spending in blockchain can occur when a user broadcasts two transactions into the network using the same coins. If the transaction where the coins are sent back to the user gets confirmed first, the other transaction becomes invalid, hence resulting in double-spending.
Double-spending is prevented in blockchain through various mechanisms such as consensus algorithms, transaction verification, waiting for sufficient confirmations, network security measures, and the role of miners.
A 51% attack refers to a potential attack on a blockchain network where a single entity or group gains control of more than half of the network's mining power. With majority control, the entity could potentially double-spend coins by manipulating the blockchain ledger.
As blockchain technology evolves, new techniques and measures to prevent double-spending are continually being developed. Innovations in consensus algorithms, transaction processing, and network architecture are all part of the ongoing effort to secure the blockchain against double-spending and other forms of fraud. However, the arms race between protectors and exploiters of blockchain systems is likely to continue.
True Tamplin is a published author, public speaker, CEO of UpDigital, and founder of Finance Strategists.
True is a Certified Educator in Personal Finance (CEPF®), author of The Handy Financial Ratios Guide, a member of the Society for Advancing Business Editing and Writing, contributes to his financial education site, Finance Strategists, and has spoken to various financial communities such as the CFA Institute, as well as university students like his Alma mater, Biola University, where he received a bachelor of science in business and data analytics.
To learn more about True, visit his personal website or view his author profiles on Amazon, Nasdaq and Forbes.