The advent of blockchain technology has revolutionized how data is stored, managed, and exchanged. Blockchain, a decentralized and distributed digital ledger, securely records transactions across multiple computers. Born out of the creation of Bitcoin by the pseudonymous person (or group) Satoshi Nakamoto, blockchain is designed to be tamper-evident and resistant to modification of data. While blockchain is most renowned for its role in facilitating cryptocurrencies like Bitcoin and Ethereum, its application extends far beyond the realm of digital currency. From supply chain tracking to decentralized finance (DeFi), blockchain technology has proved to be a game-changer in numerous industries. With its decentralized structure and promise of trustless transactions, blockchain has inherent security features built into its design. This includes cryptographic techniques, consensus mechanisms, and the unalterable nature of blockchain data. However, like any technology, blockchain isn't invulnerable. A well-designed and properly implemented blockchain is incredibly difficult to hack, but applications built on top of it, such as cryptocurrency exchanges or digital wallets, may have vulnerabilities. The security of the blockchain technology largely depends on its implementation and the measures in place to mitigate vulnerabilities. While blockchain is designed to be highly secure, it is not entirely immune to hacking. The decentralized nature, cryptographic hashing, and consensus mechanisms make it significantly difficult to hack, and any successful hacking attempts are usually limited to specific vulnerabilities or exploits. There have been instances of attacks on blockchains, though these are not common and often involve considerable effort, resources, and sophisticated strategies on the part of the attacker. A 51% attack refers to a scenario where a single entity or colluding group gains control over more than half of a network's mining hashrate or computing power. This majority control allows the entity to disrupt the network by altering the ordering of transactions, blocking transactions, or carrying out double-spending attacks. Although theoretically possible, 51% attacks are impractical on large, well-established blockchains due to the vast amount of resources required. However, smaller and less secure blockchains may be more vulnerable to such attacks. A Sybil attack occurs when a network is overwhelmed by nodes controlled by a single entity. In the context of blockchain, an attacker could fill the network with nodes they control, giving them the ability to influence the network’s functioning and reliability. While blockchain networks have measures in place to prevent Sybil attacks, such as requiring proof of work or proof of stake for a node to participate in the network, they remain a potential vulnerability that needs to be considered. In a Distributed Denial of Service (DDoS) attack, an attacker overwhelms a network with traffic, causing it to become unavailable to its intended users. Even though blockchains are decentralized and thus less susceptible to DDoS attacks than traditional centralized systems, they can still be targeted, especially at individual nodes or websites related to the blockchain. Blockchain employs cryptographic hashing, a method that transforms input data of any size into a fixed-size string of text. This is a one-way function—meaning the original data cannot be derived from the hash—making it a crucial element in ensuring the integrity and security of data on the blockchain. Each block on a blockchain contains the hash of the previous block, forming a chain of blocks. As a result, any alteration in a block’s data would not only change its own hash but also disrupt the entire blockchain, making data tampering highly noticeable and nearly impossible without controlling the majority of the network. They ensure all nodes in the network agree on the validity of transactions, making it difficult for malicious actors to manipulate the system. Common consensus mechanisms include Proof of Work (PoW) and Proof of Stake (PoS). Proof of Work requires miners to solve complex mathematical problems to add a new block to the blockchain, making it computationally and financially difficult to control a majority of the network. Proof of Stake, on the other hand, requires validators to hold and 'stake' a certain amount of cryptocurrency to propose a new block, with the size of the stake affecting the likelihood of being chosen. Immutability is a fundamental aspect of blockchain security. Once data is validated and added to the blockchain, it cannot be changed or removed. This characteristic, in combination with transparency provided by the public ledger, makes blockchain resistant to fraud and tampering. This does not mean that the data on a blockchain is always 100% correct. Rather, it means that once data has been added to the blockchain, it is extremely difficult to alter. Any changes to a block would require recomputing all subsequent blocks, a task that would require enormous computational resources, especially on well-established blockchains. Smart contracts—self-executing contracts with the terms of the agreement directly written into code—are a significant innovation of blockchain technology. However, they also present security challenges. As they are written in code, they can contain bugs or vulnerabilities that can be exploited by hackers. Notably, the DAO attack in 2016 exploited a vulnerability in a smart contract to siphon off 3.6 million Ether from the Ethereum blockchain. This incident underscored the importance of thoroughly auditing and testing smart contracts before deployment. While blockchain technology itself is secure, applications built on blockchain—like cryptocurrency wallets and exchanges—are not immune to traditional cyber threats such as malware and phishing attacks. Hackers often target end-users with malware designed to steal their private keys or trick them into sending cryptocurrency to the wrong address. Phishing attacks can also be used to trick users into revealing sensitive information like passwords and private keys. The lack of clear regulation and legal frameworks around blockchain and cryptocurrencies can make it difficult to enforce security measures and prosecute cybercriminals. As blockchain technology continues to evolve and become more mainstream, it's essential for legislation and regulation to keep pace. This would not only enhance security but also foster greater trust and confidence in the technology. While the blockchain itself is secure due to its cryptographic design and consensus mechanisms, its peripheral infrastructure—including software, hardware, and network connections—can be vulnerable to attacks. For instance, software bugs or hardware flaws can be exploited by hackers. Network connections can also be intercepted, particularly if they aren't securely encrypted. As mentioned earlier, smart contracts can contain vulnerabilities that can be exploited. These vulnerabilities often stem from coding errors or oversights during the development of the smart contract. Moreover, because smart contracts automatically execute transactions based on pre-set conditions, they can facilitate unauthorized transactions if they're manipulated or exploited. Cryptocurrency exchanges and wallets, despite not being blockchains themselves, are often conflated with blockchain security. These platforms, which are used to trade and store cryptocurrencies, have been major targets for hackers. These services can have vulnerabilities, including insecure code, weak authentication mechanisms, and insufficient encryption. Some notable incidents include the hacks of the Mt. Gox and Coincheck exchanges, which resulted in losses of hundreds of millions of dollars in cryptocurrencies. While existing consensus mechanisms like PoW and PoS provide a level of security for blockchains, they aren't perfect. For example, PoW requires significant computational power and energy, while PoS could potentially lead to centralization if a small number of entities hold a large proportion of the total tokens. New and improved consensus mechanisms are being developed to address these issues. These include mechanisms like Proof of Authority (PoA), Delegated Proof of Stake (DPoS), and others that aim to provide security while being more efficient or equitable. Regular auditing and code reviews can help identify vulnerabilities in smart contracts and other blockchain applications before they can be exploited. By using both automated tools and manual reviews, developers can detect and fix coding errors, insecure programming practices, and other potential security issues. Auditing should not be a one-time event but a continuous process. As blockchain technologies and best practices evolve, previously secure code may become vulnerable, necessitating regular reviews and updates. Good cybersecurity practices are crucial for protecting against blockchain-related hacks. This includes securing private keys, using secure and updated software, enabling two-factor authentication, and being vigilant against phishing attempts. For organizations using blockchain technology, it's important to have a comprehensive cybersecurity strategy in place. This should include measures like regular security audits, employee training, and incident response plans. While the blockchain itself is designed to be highly secure, vulnerabilities can exist in peripheral infrastructure, smart contracts, and cryptocurrency exchanges and wallets. These vulnerabilities can be exploited by hackers to gain unauthorized access or carry out fraudulent activities. However, the decentralized nature, cryptographic hashing, and consensus mechanisms of blockchain make it significantly difficult to hack, and successful hacking attempts are usually limited to specific vulnerabilities or exploits. To enhance blockchain security, measures such as improving consensus mechanisms, conducting regular audits and code reviews, and implementing cybersecurity practices are essential. Moreover, addressing the limitations of blockchain security, such as smart contract vulnerabilities and regulatory challenges, is crucial for maintaining the integrity and trustworthiness of blockchain technology. As blockchain continues to evolve, ongoing research, education, and proactive security measures will play a vital role in strengthening its resilience against potential hacks.Overview of the Blockchain Technology
Can the Blockchain Be Hacked?
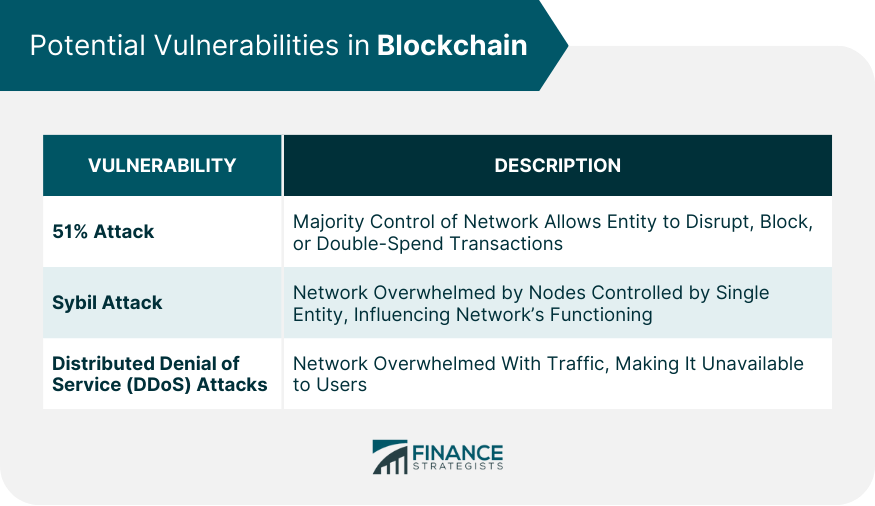
Potential Vulnerabilities in Blockchain
51% Attack
Sybil Attack
Distributed Denial of Service (DDoS) Attacks
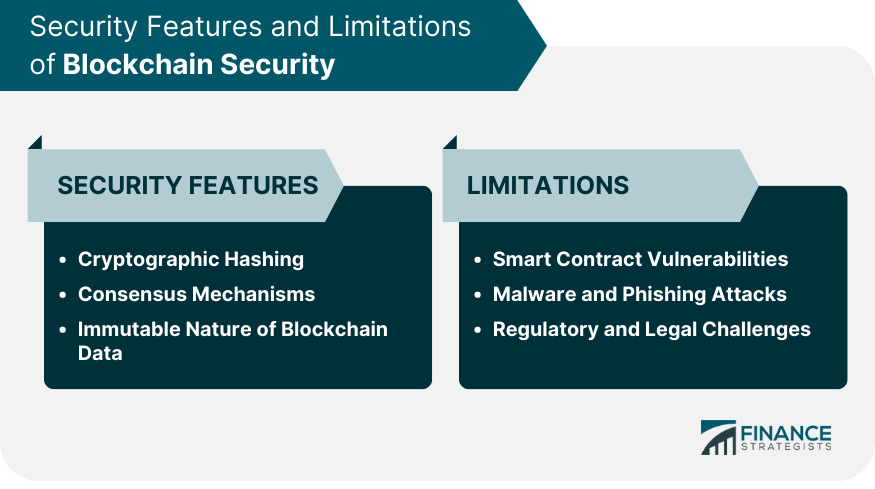
Security Features of Blockchain
Cryptographic Hashing
Consensus Mechanisms
Immutable Nature of Blockchain Data
Limitations of Blockchain Security
Smart Contract Vulnerabilities
Malware and Phishing Attacks
Regulatory and Legal Challenges
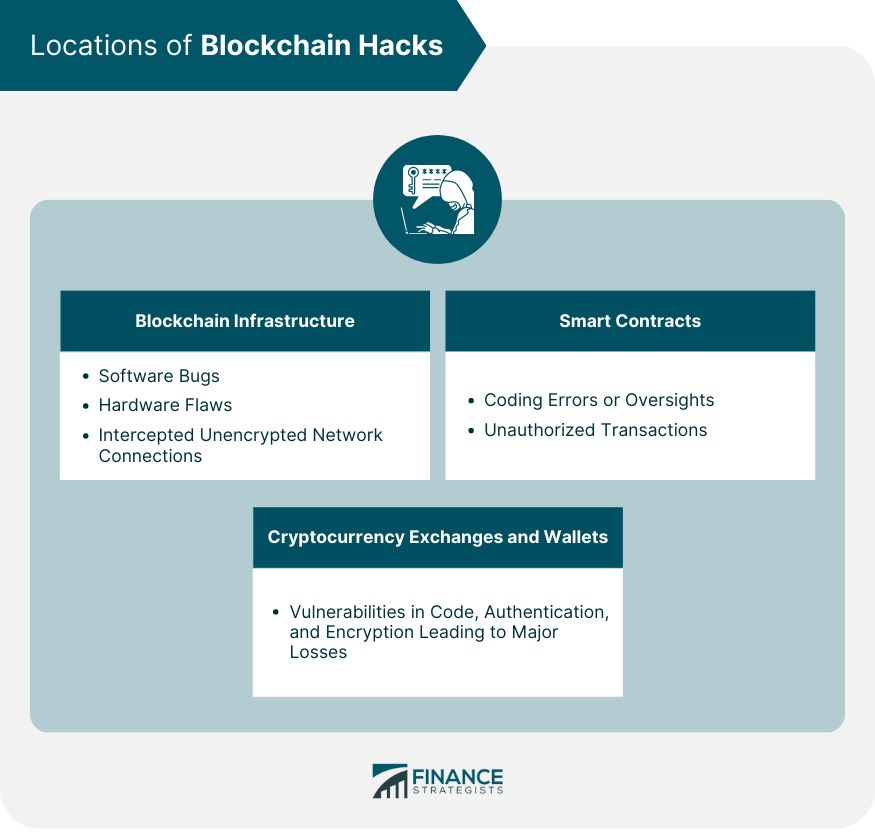
Locations of Blockchain Hacks
Blockchain Infrastructure
Smart Contracts
Cryptocurrency Exchanges and Wallets
Measures to Enhance Blockchain Security
Improving Consensus Mechanisms
Auditing and Code Reviews
Practicing Cybersecurity
Conclusion
Can the Blockchain Be Hacked? FAQs
While blockchain technology is designed to be secure and resistant to hacking, it's not entirely unhackable. The chances of a successful hack are relatively low, especially for well-established blockchains, but vulnerabilities can arise, particularly in peripheral infrastructure and smart contracts.
Potential vulnerabilities in blockchain include 51% attacks, Sybil attacks, and DDoS attacks. Additionally, smart contracts can contain vulnerabilities that can be exploited, and peripheral infrastructure like software, hardware, and network connections can also be susceptible to attacks.
Key security features of blockchain include cryptographic hashing, consensus mechanisms, and the immutable nature of blockchain data.
Limitations of blockchain security include vulnerabilities in smart contracts, susceptibility to traditional cyber threats like malware and phishing attacks, and regulatory and legal challenges.
Blockchain security can be enhanced by improving consensus mechanisms, conducting regular auditing and code reviews, and practicing good cybersecurity. A comprehensive cybersecurity strategy, along with continuous research and development, is crucial for enhancing blockchain security.
True Tamplin is a published author, public speaker, CEO of UpDigital, and founder of Finance Strategists.
True is a Certified Educator in Personal Finance (CEPF®), author of The Handy Financial Ratios Guide, a member of the Society for Advancing Business Editing and Writing, contributes to his financial education site, Finance Strategists, and has spoken to various financial communities such as the CFA Institute, as well as university students like his Alma mater, Biola University, where he received a bachelor of science in business and data analytics.
To learn more about True, visit his personal website or view his author profiles on Amazon, Nasdaq and Forbes.